Cyber Attacks
Overview

Malware . It is of cyber attack where malicious software is installed on the victim’s systems through executable files usually without the user’s knowledge. Malware includes malicious software, including spyware, ransomware, viruses, and worms. After installation, a malware can keep track of the user’s activity or can trigger codes resulting into access to sensitive information, login details, credit cards or intellectual properties by the hacker.
--- Malware Attack Types.
Ransomware — Ransomware is a type of malware that blocks access to the victim’s data and threatens to publish or delete it unless a ransom is paid.
Phishing. Phishing refers to spoofing or deceptive communications activities performed by the attackers that appear to originate from a credible source such as emails, messages, legitimate websites that are disguised. Through phishing, attackers try to fetch sensitive information, user details, credit card numbers or make fraudulent attempts. --- Phishing Attacks
Man-in-the-middle attack. An attacker hijacks a session between a trusted client and network server. The attacking computer substitutes its IP address for the trusted client while the server continues the session, believing it is communicating with the client.
DoS/DDoS. A DoS/DDoS attack aims at flooding the target website with overwhelming traffic to exhaust resources and bandwidth of the system. These are not to bring down a website but to breach a security perimeter and smoke out the online systems. This can reduce a user base or may bring down the entire network. ---- DDoS Attack Types
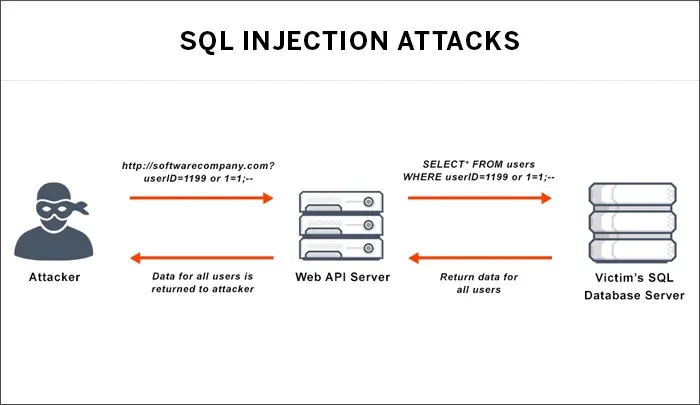
SQL Injection. It occurs when a malefactor executes a SQL query to the database via the input data from the client to server. A successful SQL injection exploit can read sensitive data from the database, modify (insert, update or delete) database data, execute administration operations (such as shutdown) on the database, recover the content of a given file, and, in some cases, issue commands to the operating system.
Zero-day exploit. Zero-day is a software security flaw which is known to the software developers. Attackers try to exploit a vulnerability before a patch or solution is implemented to capture the system with known weaknesses.
Cross Site Scripting. XSS attacks occur when a web app sends malicious code in the form of a side script to another user thus bypassing access controls of the site to same as the origin.
Business Email compromise. This is an attack to spoof business emails and gain illegal access to company accounts and ids to defraud the company or its employees.
Complete Reference Link
Classification of Cyber Attackers
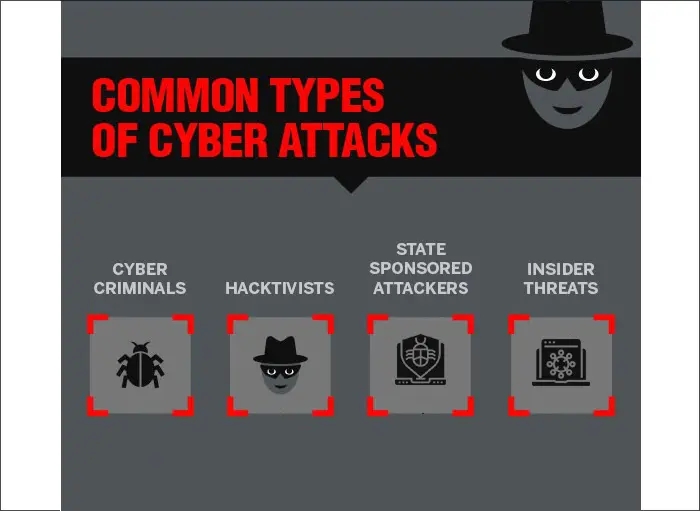
Though the purpose of a cyberattack is always malicious, the hacker may use several tools and techniques to perpetrate the attack. Depending on their intent and the end objective, cyber attackers can be roughly grouped into:
They are individuals or groups of individuals who target company information, customer data, or other critical data and try to monetize it on the dark web. They make use of sophisticated tools and techniques, use computer/mobile devices as a medium to perpetrate intelligent, hard-to-discover malicious cyberattacks.
They have a non-financial agenda to propagate. They may perform an attack to reinforce their belief system, which could be political agenda, religious ideology, or a cause which they want to be made known through their digital malfeasance. Depending on the political beliefs they hold, they can be described as progressive, ethical, or plain disruptions among other categories.
They carry out cyberattacks targeted at a particular country to destabilize its social, economic, or military administration through the support of the country of their origin. They could perpetrate lone wolf attacks as well, showing allegiance to a particular state.
They originate from employees, contractors, third-party affiliates of an organization and are hard to detect and prevent because of the trust factor involved. These attacks could be either malicious, accidental, or carried out due to pure negligence.
Further, cyberattacks fall into two groups based on the attack’s end-point:
Web-based cyber attacks, if the hacker targets a website/web application; or
The system-based cyberattack, if the attack’s purpose is meant for compromising node(s)/system(s) in a network.
Types of Cyber Attacks
➖Phishing
What is a Phishing Attack? Click Here
A Phishing Attack entails the cybercriminal sending emails that appear to be from trusted sources. The aim of this type of attack is to acquire a person’s sensitive information or to influence them into doing something.
It might, for example, feature an attachment that downloads malware onto the device when opened. Alternatively, it might provide a link to a fake website to persuade someone to hand over their information or trick them into downloading malicious software.

Types of Phishing attacks






➖ Malware
"Malware" is short for MALicious softWARE which may include spyware, ransomware, viruses, trojans, and worms. It breaches a network through a vulnerability, typically when a user either downloads an email attachment or clicks on a dangerous link that installs risky software.
Types of Malware Attacks
Malware comes in various forms depending on their end objective. In some cases, cyber-criminals use sophisticated malware to infect all the systems in the network to carry out a distributed denial of service (DDoS) attack.

A virus is the most common type of malware attack. In order for a virus to infect a system it requires a user to click or copy it to media or a host.
Most viruses self-replicate without the knowledge of the user. These viruses can be spread from one system to another via email, instant messaging, website downloads, removable media (USB), and network connections.
Some file types are more susceptible to virus infections – .doc/docx, .exe, .html, .xls/.xlsx, .zip. Viruses typically remain dormant until it has spread on to a network or a number of devices before delivering the payload.
Everyone is familiar with this term. This particular malware copies itself and is capable of spreading across the computers. They attach themselves to different programs and get executed if a user manually launches infected program. Viruses can spread via documents, script files, and cross-site scripting vulnerabilities in web apps.
Similar to a virus, a worm can also self-replicate and spread full copies and segments of itself via network connections, email attachments, and instant messages.
Unlike viruses, however, a worm does not require a host program in order to run, self-replicate, and propagate.
Worms are commonly used against email servers, web servers, and database servers.
Once infected, worms spread quickly over the internet and computer networks.
Trojan horse programs are malware that is disguised as legitimate software.
A Trojan horse program will hide on your computer until it’s called upon.
When activated, Trojans can allow threat actors to spy on you, steal your sensitive data, and gain backdoor access to your system.
Trojans are commonly downloaded through email attachments, website downloads, and instant messages.
Social engineering tactics are typically deployed to trick users into loading and executing Trojans on their systems. Unlike computer viruses and worms, Trojans are not able to self-replicate.
Also called a Trojan Horse, is a malicious program hiding in a legitimate program. The difference between normal viruses and trojans is trojans can’t replicate. Trojans not only launch an attack, but also create a back door to exploit for future attacks. For instance, a trojan could be designed to create a high-numbered port, which would allow the attacker to execute a new attack..), use the computer in botnets, and even install more malware!
Ransomware is a type of malware designed to lock users out of their system or deny access to data until a ransom is paid.
Crypto-Malware is a type of ransomware that encrypts user files and requires payment within a time frame and often through a digital currency like Bitcoin.
Ransomware is a type of malware that blocks access to the victim’s data and threatens to publish or delete it unless a ransom is paid.
This makes a computer system captive until the user pays money, usually in bitcoins. It restricts by encrypting the files on the hard drive, or by locking the entire system, displaying the message. It can travel through the network that might seem like a normal computer worm.
WannaCry and Maze ransomware are recent examples of how malware could wreak havoc, forcing many corporations to shell out bitcoins and money to pay for retrieving their compromised machines and data.
Adware is a software program used by businesses as part of their marketing efforts. It usually manifests as advertisements or banners displayed while applications are running. When you browse a website, adware can automatically download itself to your device.
This type of cyberattack is designed to collect information on the victim, particularly their browsing habits. Spyware tracks everything you do without your consent or knowledge and delivers the information directly to a remote user. It can install other malicious applications onto your system via the internet.
They can monitor through keystrokes (saving the keypress event of users through a specific software and using it for personal gain), data harvesting (retrieving users’ account information, login details, etc.), and much more. Spyware can also modify the existing software’ or browser’s security settings, which results into interfering with network connections. If an existing software is vulnerable, it is easy for spyware to invade it.
Botnet, short for roBOT NETwork, is a group of bots, which are any type of computer system attached to a network whose security has been compromised.
They are typically controlled remotely.
Bots are designed to automatically perform various tasks. The most familiar bots belong to the search engines that crawl through the websites and list them as per the SEO norms. But it is possible (and quite common these days) that bots are used in botnets, that are basically collections of computers being controlled by the third parties. These could be prevented using CAPTCHA (“I am not a robot”) tests, that most authentic sites perform these days.
Rootkit is a type of malware that is designed to gain access and control a computer system without getting detected by the security programs. Once it is installed, the attacker can execute the files, steal the sensitive information, and modify the system configurations. It is capable to even edit the security software! It can smartly hide its presence and so is difficult to get detected, prevented, and removing it.
Most programmers are familiar with this term. It is just an error that does not allow a small program or an application to run smoothly. If a bug is a major one, it can cause a system crash. The most severe among them all is the security bugs that can bypass user authentication, steal the data, or override access privileges. It could be prevented using code analysis tools and quality control, along with a hands-on knowledge of coding that deals with such kinds of issues

➖SQL Injection
The SQL injection attack has become a common problem for database-driven websites. These attacks occur when a SQL query is executed by a cyber criminals and issued to a database, delivered from the client to the server via the input data.
When a SQL injection attack is successful, sensitive information can be read, stolen, modified, inserted, updated, or deleted. Cyberattackers can also execute administration processes, like shutdown, on the database; recover content from any given file; and even issue commands to the operating system.
Ref: Click Here

➖Denial of Service or Distributed Denial of Service Attacks
DoS: This attack is used by hackers to overload a system’s resources, Servers or Networks, which causes the system to become unresponsive to service requests.
DDoS: Overwhelming the target with a flood of activity from hundreds or even thousands of devices in a botnet. It meaans targets the system’s resources, but the source of the launch comes from a large number of host machines, each of which is infected and under the control of the cyberattacker.
Work in partnership with botnets

Types of DoS/DDoS Attacks






➖Cross-Site Scripting (XSS)
They are a group of attacks where the attacker injects code or malicious scripts directly into a benign website without attacking the website itself. The attacker writes the script in JavaScript, Flash, Ajax, etc.
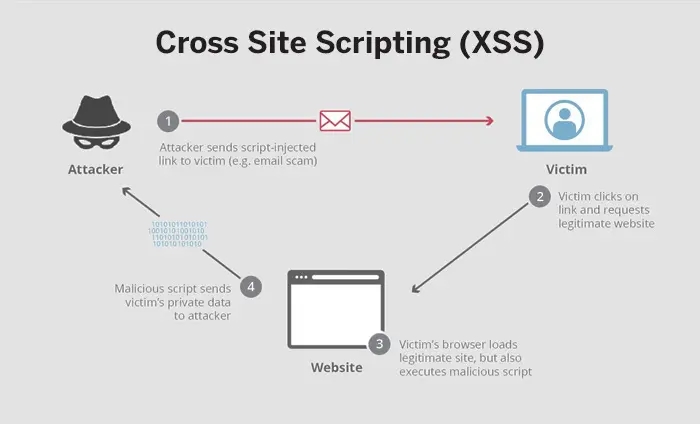
Types of XSS Attacks
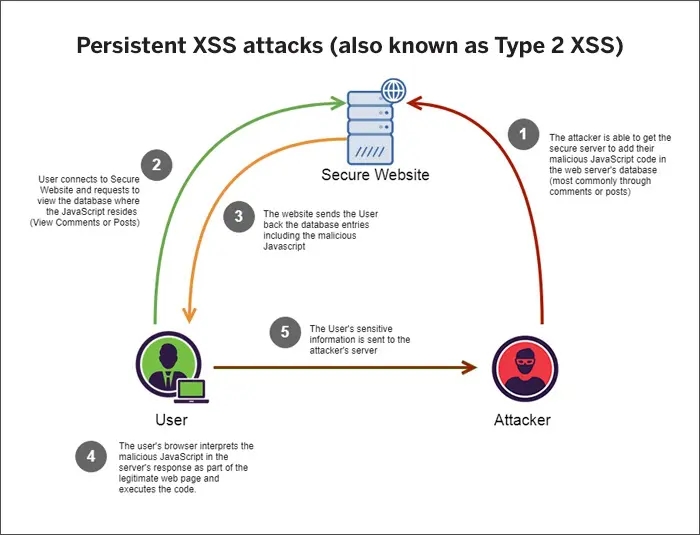
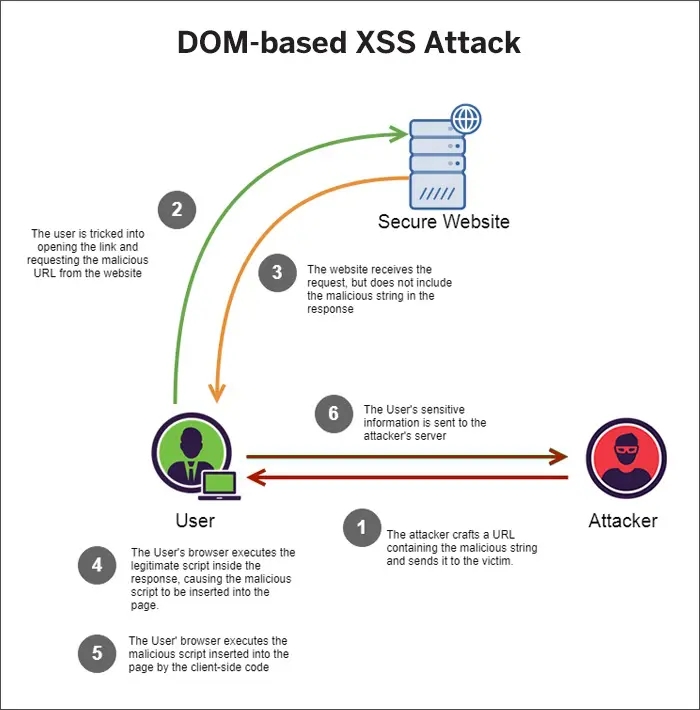
➖Man-in-the-Middle (MiTM) Attack
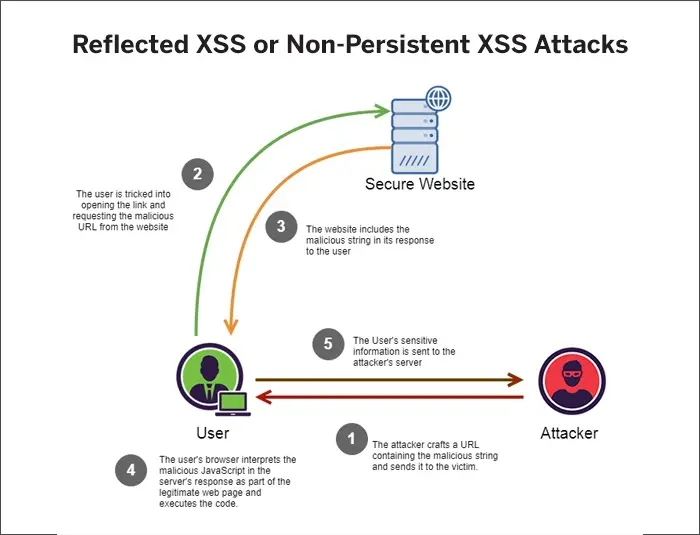
This attack is also known as eavesdropping attack. Attackers insert themselves secretly between the user and a web service they’re trying to access. They then can filter and steal data. For instance, an attacker might set up a Wi-Fi network with a login screen designed to mimic a hotel network and as soon as a user logs in, the attacker may steal the information, such as a banking password, that user sends on that network.
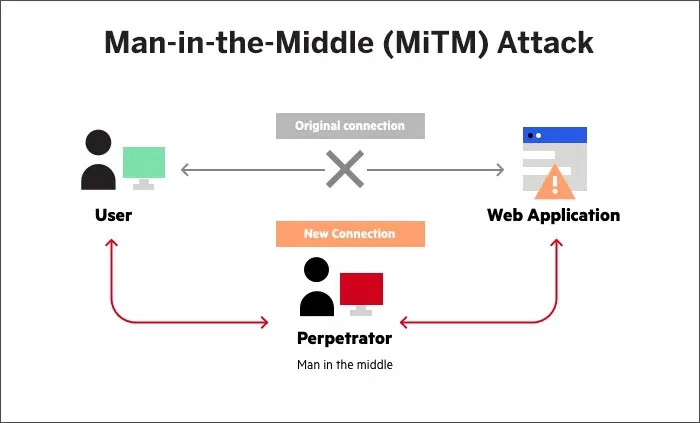
This attack is also known as eavesdropping attack. Attackers insert themselves secretly between the user and a web service they’re trying to access. They then can filter and steal data. For instance, an attacker might set up a Wi-Fi network with a login screen designed to mimic a hotel network and as soon as a user logs in, the attacker may steal the information, such as a banking password, that user sends on that network.
This attack comes in many flavors, like IP and DNS spoofing, replay attack, and session hijacking.
Types of MiTM Attacks
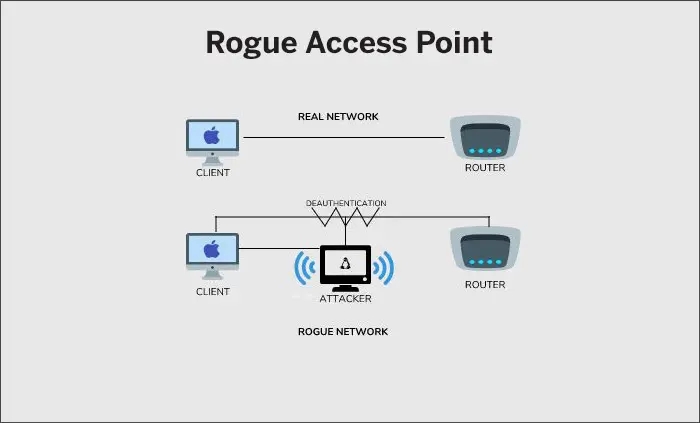
The rogue access point is an unauthorized node in the network but is still somehow operating. Using such open wireless access points, attackers may try to gain access to nearby devices. They usually come with no encryption or authentication, so that maximum devices in proximity can connect. The attacker, thus, compromises the network data.
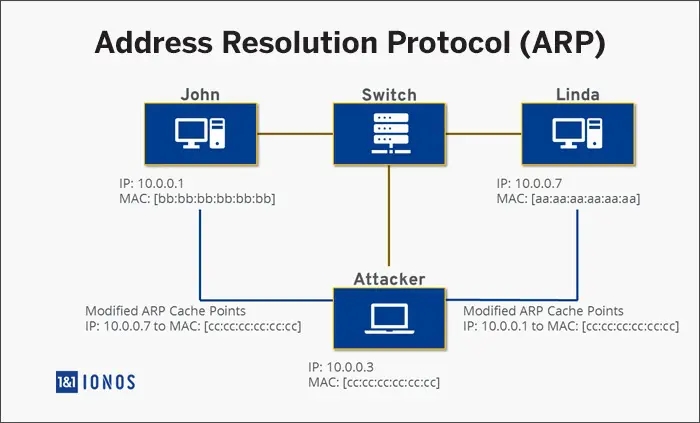
ARP resolves system IP addresses to physical media access protocol (MAC) addresses in LAN. Two hosts talk to each other by resolving IP addresses to the MAC address by referencing ARP. Using ARP spoofing, the attacker sends false/spoofed ARP messages. This causes their MAC address to map with the address of a legitimate computer in the network. This results in the attacker obtaining information intended for the original system, intercepting and modifying the data during transit.
Here, a DNS query is sent to all devices in the network in the same broadcast domain. The snooper carries out mDNS spoofing attack on LAN, just like ARP spoofing, with users not necessarily having to remember the addresses to which they connect. The attacker uses this protocol’s simplifying exercise to request with fake data and connects to the system as a trusted network. The victim’s system will show the attacker’s device as a trusted network, which can then control the device.
The attacker perpetrates MiTM attacks using several techniques. These include sniffing, where attackers employ packet capture tools and inspect network packets not intended for them. Additionally, the attacker uses packet injection to insert malicious packet data into the network stream, mixed with the legitimate data packets to evade recognition.
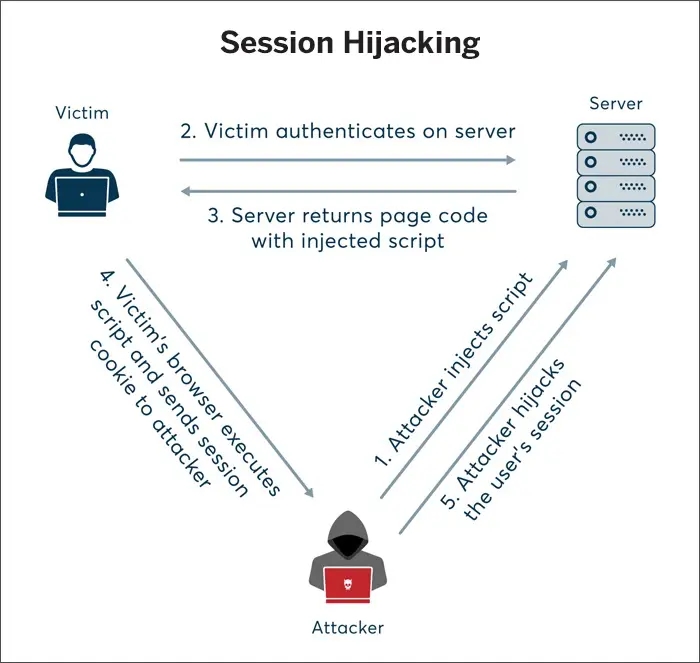
Session hijacking is a prevalent MiTM attack vector. Through XSS, the attacker gains access to user session token and impersonates the user’s activities. After the hacker gets access to the session token, they have complete access to the user’s rights on the application.
SSL stripping, as the name suggests, involves stripping the secure layer from HTTPS to allow ARP or DNS spoofing. Attackers intercept packets to alter their secure HTTP requests to their non-secure HTTP equivalent, which passes on sensitive information as unencrypted, plain text information.
➖Zero-Day Attack
This attack occurs when a network’s vulnerability is announced but a patch or solution is yet to be implemented. Attackers sneak-in during this window of time.
Best Practices to Prevent Cyber Attacks
In the face of complex security threats and newly emerging attack techniques, howsoever robust a system/web application may be, it is never totally secure. This overarching reality, however, should not deter us from ingraining cybersecurity best practices, which act as the first line of defense in the event of a potent cyberattack.
Based on the observations made in the sections on different cyberattacks, let us have a look at the practices, techniques, and policies to prevent cyberattacks:
Use a comprehensive anti-virus solution that tracks your employees’ online activities, websites they visit, and attachments they open, etc. to keep malware attacks at bay.
Install a robust firewall and configure it appropriately to facilitate a secure online experience for your employees. A third-party firewall (in addition to the default internal firewall) gives the extra security cushion needed for your business. An email quarantine engine would help identify spam/phishing sources before delivering it to employees. You may also apply advanced security features such as runtime application self-protection to prevent attacks in real-time.
Monitor your network regularly and investigate any suspicious activity immediately to prevent any untoward incident. Investing in comprehensive security suites, like AppSealing, can make all the difference between preventing a cyberattack and regretting the losses from a preventable cyberattack.
Prepare a detailed cybersecurity policy document and adhere to it as far as possible.
Train and educate your stakeholders, including employees and vendors, on how to conduct themselves safely while being online and make them aware of safe browsing practices and security policies.
Schedule regular data backup (including cloud data) as an organizational practice and store the backup in a separate server. This habit prevents critical data loss in the event of a cyberattack, including ransomware attacks.
Enforce strong and safe password practices to prevent security breaches, especially with multiple devices accessing data from company networks. Strong passwords are still one of the most elementary ways to enforce cybersecurity across the organization.
Engage with security specialists and conduct a vulnerability assessment and penetration testing to identify loopholes in your application and undertake remedial measures to prevent your application from becoming a source of perpetrating malware/XSS attack.
In short, adopting a proactive approach is the only sustainable way to handle contemporary security threat scenarios. This approach should build a robust security architecture that addresses both network and application security needs of an organization.
Reference Links
Malware Types --- Click Here
Last updated